May 18, 2022 Update
The Conti group’s data leak page has been updated. As of today, the page states that 100% of the stolen data has been published. According to the U.S. Department of Health and Human Services, 119,513 people are impacted by this data breach.
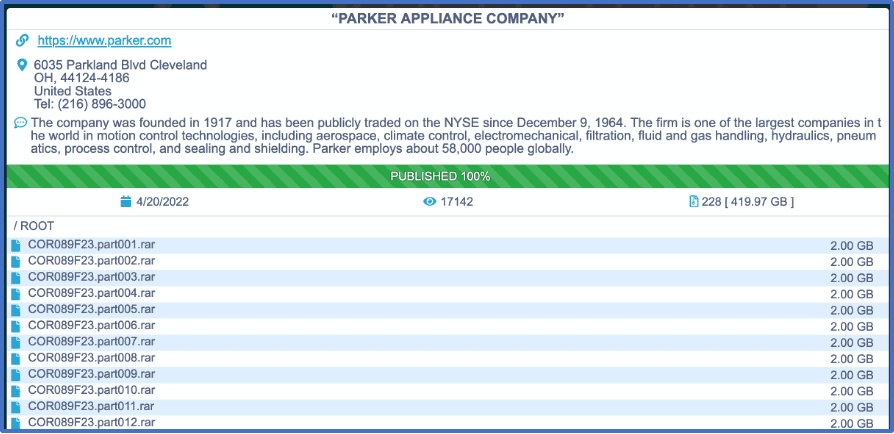
The size of the data cache purportedly released to the dark web for open access is now 419.97 GB. It would appear that the data leak page has been viewed over 17,000 times.
Individuals who have received a Data Breach Notice from Parker-Hannifin in connection with this cyber-security incident should remain vigilant in oversight of their financial and medical information and be on the alert for any unusual charges or contacts indicating a use of their personal information.
Original Story
On May 12, 2022, Parker-Hannifin reported a data breach to the California Attorney General’s Office affecting current and former employees, their dependents, and others.
The personal information that may have been accessed and taken includes:
- Full Names
- Social Security Numbers
- Dates of Birth
- Addresses
- Driver’s License Numbers
- S. Passport Numbers
- Bank Account and Routing Numbers,
- Online Username and Password
If you are a current or former enrollee of Parker’s Group Health Plan (or a health plan sponsored by an entity acquired by Parker), there may also have been unauthorized access and theft of:
- Health Plan Enrollment Information
- Health Insurance Plan ID Numbers
- Dates of Coverage
According to the company, for a smaller subset of individuals, the following sensitive information may also have been accessed and acquired:
- Dates of Medical Coverage
- Dates of Medical Services
- Provider Names
- Claims Information
- Medical and Clinical Treatment Information
The full text of the Parker-Hannifin Notice of Data Breach can be found here. More details are included in the company’s public statement, located here.
Parker’s public statement disclosed that “an unauthorized party gained access to Parker’s IT systems” from March 11-14, 2022. Files with the sensitive personal, financial, and medical information listed above may have been accessed and taken. Parker-Hannifin began notifying affected individuals on May 13, 2022, two months after the data breach. All notified individuals are being offered two-years of credit monitoring. There is a deadline for enrollment.
Conti Ransomware Group Reported Behind Hack
While not included in Parker-Hannifin’s public statements about this incident, Security Week reports that Parker’s attack was perpetrated by the Conti ransomware group. The group published 5 GB of the stolen files on the dark web, which purportedly was only 3% of the data taken. Typically, this sort of publication is done to prove the personal data has been successfully stolen.
The FBI has been warning companies about the threat posed by the Conti group for over a year. It issued a Flash Alert about Conti ransomware attacks in May, 2021, and a Cybersecurity Advisory on September 22, 2021, which was updated most recently on March 9, 2022.
Special California Laws Protect You From Data Breach Harms
If you are a California resident and received a Notice of Data Breach from Parker-Hannifin, you may be entitled to between $100 and $1,000 plus actual damages resulting from the negligent release of your confidential information. California has unique state laws, including the California Consumer Privacy Act (CCPA) and the California Confidentiality of Medical Information Act (CMIA) that compensate individuals whose confidential and sensitive data have been accessed in ransomware events.
Participants in data breach lawsuits can recover damages, injunctive relief (to make sure that the business has reasonable security practices to protect consumer data from being leaked again) and anything else the court concludes is necessary to compensate data breach victims and prevent these harms from occurring again.
If I follow the steps in the Parker-Hannifin Data Breach Notice, will that prevent my personal information from being sold on the dark web?
“Dark web” monitoring can sometimes tell you if your information is being offered for sale to cyber thieves but cannot actually prevent the sale of that information. Unfortunately, if you are the victim of a data breach you will still need to be on the lookout. You must remain ever watchful for unapproved credit card charges, identify theft, tax fraud and other illegal uses of your personal information.
As Electronic Personal Data Doesn’t Degrade, Two Years Of Identity Theft Services May Not Be Enough
Cybercrimes present an attractive target for hackers: Data can be bought and sold anonymously, and the going rate per personal record is low (under $20 per record, depending on the type of information according to Privacy Affairs Dark Web Index of 2021). Certain critical types of personal information – like social security numbers, names, and birth dates – are almost impossible to change. Thieves may choose to wait years to capitalize on compromised personal data. The longer cyber thieves can go undetected, the more they stand to profit from their illegal activities.
“The effects of a health data breach on consumers outlast the initial breach.” Source: R. Bonta, California Attorney General, BULLETIN: Obligation to Proactively Reduce Vulnerabilities to Ransomware Attacks and Requirements Regarding Health Data Breach Reporting (2021).
Not every data breach will lead to identity theft. But once you know your data has been disclosed, it is reasonable to be concerned that your data will be used to cause you significant financial losses. Compromised data also increases the risk of hacking, phishing, and increased anxiety over future losses and identity theft.
Corporations Should Be Held Accountable For Data Breaches
When businesses decide to collect and keep personal data about California employees and their dependents, under California law they take on the obligation to protect that information and keep it safe from hackers, thieves, and other criminals.
This personal data is incredibly valuable, both to businesses and to criminals who want to sell that information on the dark web to identity thieves and other black marketeers. However, “it is clear that many organizations need to sharpen their security skills, trainings, practices, and procedures to properly protect consumers.” The stakes are high: Data breach victims are more likely to also be victims of additional fraud. Source: K. Harris, former Attorney General, California DOJ, California Data Breach Report 2012-2015 (2016).